Understanding Zero Trust Architecture (ZTA) and Why It’s Critical for SMBs in 2024
This blog post dives into Zero Trust Architecture (ZTA), its benefits, and how small and medium businesses (SMBs) can begin to implement it, along with practical advice for SMBs.
CYBERSECURITYSECURITY BEST PRACTICESCYBERSECURITYTIPSSMALL AND MEDIUM SIZED BUSINESS
Weston Wilson
11/11/20245 min read
As cybersecurity threats continue to evolve, many businesses are reevaluating their approach to network security. One increasingly popular—and effective—security model is Zero Trust Architecture (ZTA). Originally proposed around 2010, Zero Trust only recently gained widespread attention and adoption, especially after it was formalized in the NIST SP 800-207 guidelines and highlighted in the US Federal Mandate M-22-09, which requires federal agencies to implement ZTA by the end of fiscal year 2024. Now, as more and more businesses, including small and medium-sized enterprises (SMBs), look to bolster their defenses, Zero Trust is becoming a critical concept to understand and adopt.
At SystemSecure, Ltd., we specialize in helping SMBs navigate complex cybersecurity challenges. In this post, we'll break down what Zero Trust is, why it’s important for your business, and how you can begin implementing aspects of this architecture to strengthen your security posture.
What Is Zero Trust Architecture (ZTA)?
Zero Trust is a cybersecurity model based on the principle that no device or user should be trusted by default, whether inside or outside the network. The traditional "castle-and-moat" security model assumes that once a user or device is inside a company’s network, they are inherently trusted. Zero Trust, on the other hand, assumes that every access request—whether it originates from inside or outside the network—could potentially be malicious. Therefore, each request must be authenticated, authorized, and continuously validated before granting access.
The core idea is simple: never trust, always verify. This means that instead of allowing access to systems based on network location or device type, each device, user, and connection is subject to strict verification processes before granting access to any resource. To achieve this, several technologies and strategies are used, including multi-factor authentication (MFA), least-privilege access controls, identity and access management (IAM), and continuous monitoring of activity.
Why Is Zero Trust Important for SMBs?
While Zero Trust was originally designed with larger enterprises and government organizations in mind, it has become increasingly critical for small and medium-sized businesses (SMBs) as well. SMBs are prime targets for cybercriminals because they often lack the advanced security infrastructure and resources that larger enterprises have. Here’s why adopting Zero Trust is crucial for SMBs:
Protect Against Insider Threats and External Attacks
Zero Trust reduces the risk of both insider threats (malicious or compromised employees) and external attacks (hackers exploiting weak points in the network). Since Zero Trust doesn't trust any device or user by default, it creates an additional layer of defense against unauthorized access and data breaches.Enhanced Security for Remote and Hybrid Workforces
With the rise of remote work and hybrid work models, traditional perimeter-based security approaches are no longer sufficient. Zero Trust enables SMBs to maintain secure access control regardless of where employees or devices are located—whether in the office or working remotely. By requiring continuous verification of every user and device, Zero Trust ensures that remote workers have the same level of security as those working on-site.Adaptability to the Modern Threat Landscape
Cyber threats are becoming increasingly sophisticated. Ransomware attacks, phishing campaigns, and credential stuffing are just a few examples of the tactics used by cybercriminals to exploit vulnerabilities. Zero Trust provides a proactive approach by reducing the attack surface and continuously monitoring user and device activity for anomalies, making it harder for attackers to move laterally within your network.Compliance with Industry Regulations
Many industries, including healthcare, finance, and retail, have strict compliance requirements that mandate robust data protection measures. Zero Trust helps businesses meet these requirements by ensuring only authorized users and devices can access sensitive information, while also enabling detailed audit logs and reporting capabilities.
How Zero Trust Works: Key Principles
Zero Trust relies on several principles and technologies to function effectively. Here are the core components:
Verification of Every User and Device
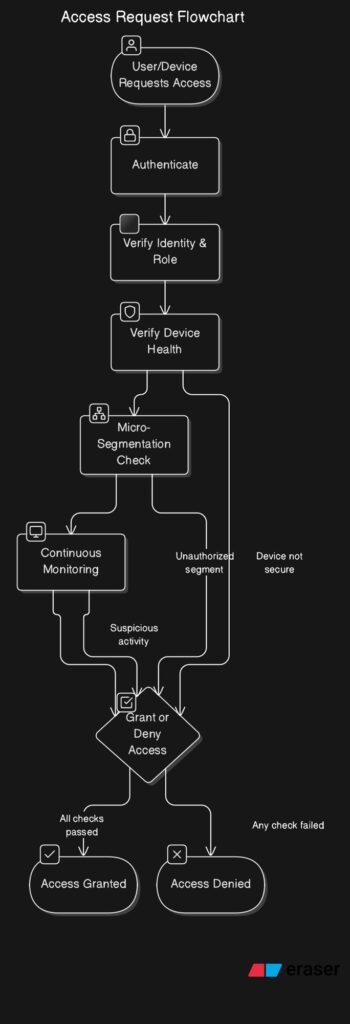
Every user, device, and application is continuously verified through various methods, such as multi-factor authentication (MFA), biometrics, behavioral analytics, and device health checks. If any of these factors fail, access is denied.Least-Privilege Access Control
In a Zero Trust environment, users are given the minimum level of access necessary to perform their job functions. This reduces the risk of damage in case an account or device is compromised. For example, an employee working in accounting should only have access to financial data, not marketing materials or HR files.Micro-Segmentation
Instead of creating broad, all-encompassing security zones, Zero Trust uses micro-segmentation to divide the network into smaller, isolated segments. This limits the potential damage of a breach and makes it harder for attackers to move laterally across the network.Continuous Monitoring and Adaptive Access
Zero Trust is not a one-time security check; it involves continuous monitoring of user behavior, device posture, and traffic patterns. If anything suspicious is detected (e.g., access from an unusual location or time), the system can automatically adjust access permissions or trigger security alerts.
How to Begin Implementing Zero Trust for Your SMB
While Zero Trust may sound complex, SMBs don’t need to implement every element all at once. Here’s how to get started:
1. Assess Your Current Security Posture
Begin by understanding your current network infrastructure and identifying areas where Zero Trust principles can be integrated. Start with your most critical assets—such as sensitive data, customer information, and intellectual property—and prioritize securing them.
2. Implement Multi-Factor Authentication (MFA)
A key component of Zero Trust is ensuring that users are who they say they are. Implement MFA for all employees, especially for accessing cloud services, email accounts, and other critical systems. This is an easy and effective first step toward Zero Trust.
3. Adopt Identity and Access Management (IAM) Solutions
IAM tools help you control who can access what resources, and under what conditions. Ensure that access controls are set based on roles and responsibilities, and use single sign-on (SSO) solutions for easier management.
4. Segment Your Network
Use network segmentation to limit access to sensitive data and systems. For example, segmenting employee data from financial data or isolating your production systems from less critical business functions can help contain breaches if one segment is compromised.
5. Monitor and Respond to Anomalies
Continuous monitoring of user and device behavior is critical to Zero Trust. Invest in Security Information and Event Management (SIEM) systems that help you detect suspicious activity and respond quickly to potential threats.
6. Educate Your Employees
Educate your staff about the importance of security and the role they play in maintaining Zero Trust principles. Regular training on topics like phishing attacks, password management, and secure device usage can go a long way in strengthening your overall security posture.
Conclusion
Zero Trust Architecture is not just a buzzword; it’s a critical cybersecurity framework that can help small and medium businesses defend against the increasing range of cyber threats. While transitioning to a Zero Trust model may take time, the benefits far outweigh the effort, especially for SMBs seeking to protect their sensitive data and systems from malicious actors. By adopting Zero Trust principles like multi-factor authentication, least-privilege access, and continuous monitoring, your business can significantly enhance its security posture and reduce the risk of costly breaches.
At SystemSecure, Ltd., we specialize in helping SMBs implement Zero Trust strategies tailored to their unique needs. Contact us today to learn how we can help you start your journey toward a Zero Trust environment and strengthen your cybersecurity defenses.